What is a privacy password. Protect data on Android phones and tablets. Code to add a consent checkbox to the form
Probably every programmer at least once in his life has encountered the need to hide information inside an application. These could be encryption keys for decrypting program components, API Endpoints addresses, strings that are best hidden to make it difficult for the reverser to work. This is very difficult to do on Android, but you can make it significantly more difficult to extract them.
Let's start with the fact that, despite the promise to show effective methods hiding information in the application, I still strongly recommend not to do this, at least until it becomes clear that you simply cannot do without it. No matter how sophisticated methods you use to hide information, it will still be possible to extract it. Yes, you can use many obfuscation techniques, use encryption or files hidden inside the application (we will talk about all of this), but if someone sets themselves the goal of revealing the secrets of your application, then if they have sufficient qualifications, they will do it.
So it’s definitely not worth putting all passwords, encryption keys and other really important information into the application code. Do you need to give your application access to some web service? Use its API to obtain a service token the moment you connect to it. Does the application use a special hidden API of your service? Make it request its URL from the service itself and this URL is unique for each copy of the application. Are you making a file encryption application? Request an encryption password from the user. In general, by any means, make sure that there is no information inside the application that could lead to hacking of your accounts, your web service or user data.
And if you still decide to embed important data into the application code and do not want them to be seen, there are several recipes on how to do this, from the simplest to the truly complex.
Saving strings in strings.xml
This is probably simplest method hiding rows. The point of the method is that instead of placing a string inside a constant in the code, which will lead to its detection after decompilation, place it in the res/values/strings.xml file:
And from the code access via getResources():
String password = getResources().getString(R.string.password);
Yes, many application reverse tools allow you to view the contents of strings.xml , so it’s better to change the string name (password) to something harmless, and make the password itself look like a diagnostic message (something like Error 8932777), and even use it only part of this string, splitting it using the split() method:
String string= getResources().getString(R.string.password).split(" "); String password = strings;
Naturally, it is also better to give the variables harmless names, or simply enable ProGuard, which will shorten their names to one or two-letter combinations like a, b, c, ab.
Breaking lines into parts
You can not only use parts of lines, but also split them up and then put them together. Let's say you want to hide the line MyLittlePony in your code. It is not at all necessary to store it in one single variable; break it into several lines and scatter them across different methods or even classes:
String a = "MyLi"; String b = "ttle"; String c = "Pony"; ... String password = a + b + c;
But there is a danger of running into compiler optimizations that will put the string together to improve performance. Therefore, it is better not to apply the static and final directives to these variables.
Encoding data using XOR
To further confuse the reverser, the lines can be xed. This is the favorite method of beginning (and not only) virus writers. The essence of the method: we take a string, generate another string (key), decompose them into bytes and apply the exclusive OR operation. The result is an XOR-encoded string that can be decoded by again using exclusive OR. In code it might all look something like this (create a StringXOR class and put these methods in it):
// Encode the string public static String encode(String s, String key) ( return Base64.encodeToString(xor(s.getBytes(), key.getBytes(), 0); ) // Decode the string public static String decode(String s, String key) ( return new String(xor(Base64.decode(s, 0), key.getBytes())); ) // The XOR operation itself private static byte xor(byte a, byte key) ( byte out = new byte; for (int i = 0; i< a.length; i++) { out[i] = (byte) (a[i] ^ key); } return out; }
Come up with a second line (key) and use it to encode the lines that you want to hide (for example, let these be the lines password1 and password2 , key 1234):
String encoded1 = StringXOR.encode("password1", "1234"); String encoded2 = StringXOR.encode("password2", "1234"); Log.e("DEBUG", "encoded1: " + encoded1); Log.e("DEBUG", "encoded2: " + encoded2);
When you open Android Monitor in Android Studio, you will find lines like:
Encoded1: RVRCRQ== encoded2: ACHBDS==
These are the original strings encoded using XOR. Add them to the code instead of the original ones, and when accessing strings, use the decoding function:
String password1 = StringXOR.decode(encodedPassword1, "1234");
Thanks to this method, the strings will not be openly located in the application code, but decoding them will also not be difficult at all, so you should not rely entirely on this method. And the key will also have to be hidden somehow.
Continuation is available only to members
Option 1. Join the “site” community to read all materials on the site
Membership in the community within the specified period will give you access to ALL Hacker materials, increase your personal cumulative discount and allow you to accumulate a professional Xakep Score rating!
In this article we will talk about the privacy policy on the site.
Privacy policy for a website or landing page?
Why do you need a PC?
If you are advertising or planning to create advertising on Vkontakte, Target Mail ru and collect personal data of visitors on your landing page (name, email, phone number, etc.), then you need to add a privacy policy to the site in order to undergo moderation (to you have been admitted to shows) on these networks.
Because in Russia there is Federal Law No. 152 - Federal Law of the Russian Federation “On Personal Data”. By law, personal data must only be collected for a specific purpose and must be protected, meaning it must not be passed on to other people.
In this policy, which you add to the site, you must state that you collect contact information for the purpose of, for example, subscribing to an email newsletter and that this contact information will in no case be passed on to third parties. After you add this policy on , then you will increase the likelihood of passing moderation in advertising networks.
Generate Privacy Policy
Landing page privacy policy
How to add a PC to a landing page in a pop-up window (modal window). For a landing page (meaning a one-page site for advertising), it is important that the user does not go to other pages, so we will look at the example of creating a pop-up window.
Steps to create a modal window:
- Open landing page
- Open bootstrap documentation (in English)
- Find the code in the bootstrap documentation “modal window” (Modal) and paste it into our landing page.
In this case, the modal window consists of 2 parts:
- links or buttons that add and open this modal window;
- the modal window itself.
One important point: in addition to bootstrap styles, bootstrap JavaScript and JQuery must be loaded. Then a modal window will open correctly on the landing page.
So what should we get?
A modal window on the landing page that opens when you click on the PRIVACY POLICY link using the example of my landing page lp.site. Now I have changed the page a little.
To work with the landing page, I’ll take the “Games for Girls” landing page that we created.
For ease of use, open the following windows in your browser:
- your server
- your landing page
- www. getbootstrap. com in the JavaScript menu on the right select Modal
In the bootstrap documentation, in the Modal section, go down and find Live Demo, copy the code under this caption. Open and paste the code into a new window. In NotePad++, select SYNTAX, H, HTML from the menu for ease of use.
In this code we change “Launch Demo Modal” to “Privacy Policy”. Then we change the button
Next you need to change the modal window itself. Find “Modal Title” in the code below and insert “Privacy Policy” instead of this inscription. Instead of "Close" write "Close". Remove the Save Change button code completely. Save.
In the code with the tag
Next we find the last tag
this is the dividing line. Save your changes.
Example privacy policy text
Copy the code below, there is already an example text in the html
Result
Let's go to our landing page and refresh the page in the browser. A PRIVACY POLICY link has appeared below the form with the button. Click on the link. A modal window opens with the text of the policy. On my landing page you can download the link in the modal window pdf file with the text of the privacy policy. If you want to do the same, copy the text on my landing page, paste it into Word document, change the text to suit you.
If you collect email on the site, you must indicate your email in the privacy policy. Same with the phone number.
Privacy Policy for the Site
For a website, everything is simpler because you don't need to create a modal window. Just take the PC text and create a separate page. On new page publish the text and at the bottom of the site in the footer put a link to the page with the PC text.
Conclusion
This is how a PC is added to the site using the bootstrap framework.
You can see how the modal window with the privacy policy works on the website lp. rek9. ru
Currently, a smartphone contains a huge amount of personal information its owner, the protection of which should be approached with full responsibility. This information is especially vulnerable if the smartphone is lost or stolen. Attackers can get hold of not only personal correspondence and contacts of the smartphone owner, but also photographs of varying degrees of frankness, as well as data about bank cards and much more.
All the settings that will be discussed in this material are located in “Settings -> Security -> Screen Lock”.
PIN code
This is a set of 4 to 16 digits that the device will ask you to do when you try to unlock the screen. The more numbers it contains, the higher the degree of protection, but it may be inconvenient for you to unlock the screen every time in order to view a message, calendar, and so on. For basic security, you can specify four digits.
Password
This option does not limit the user to just numbers. If you want the device to be unlocked by entering a phrase or an entire sentence, this method is the most preferable. But keep in mind that typing words multiple times a day may be more tedious than other security options, but more secure than a digital password.

Face control
Despite the fact that such protection is as simple as possible, at the moment it may not work ideally in all situations. For this reason, the system will prompt you to duplicate it with a password of numbers or letters to unlock it. The essence of how this feature works: the device will take a photo of your face, and, when you try to unlock it, will compare the image received from front camera with a reference image, which is specified during setup. Unfortunately, this feature is not available on devices without a front camera.

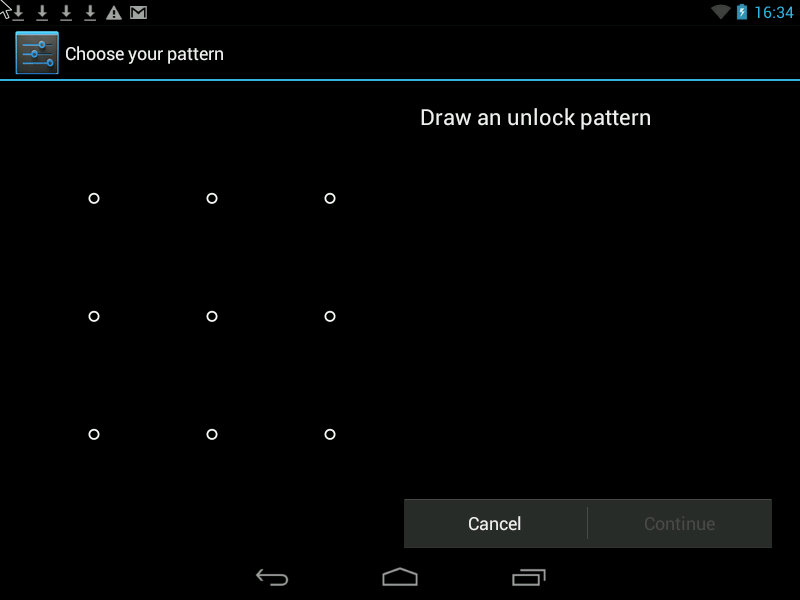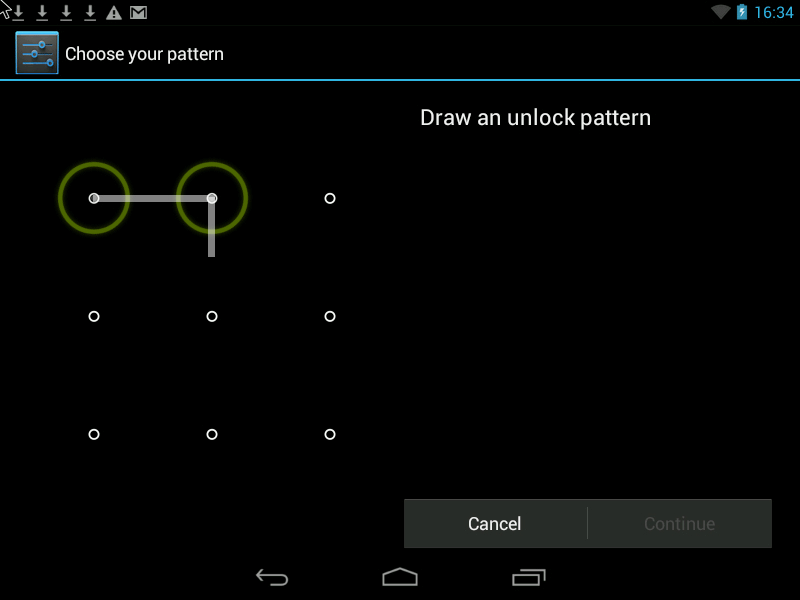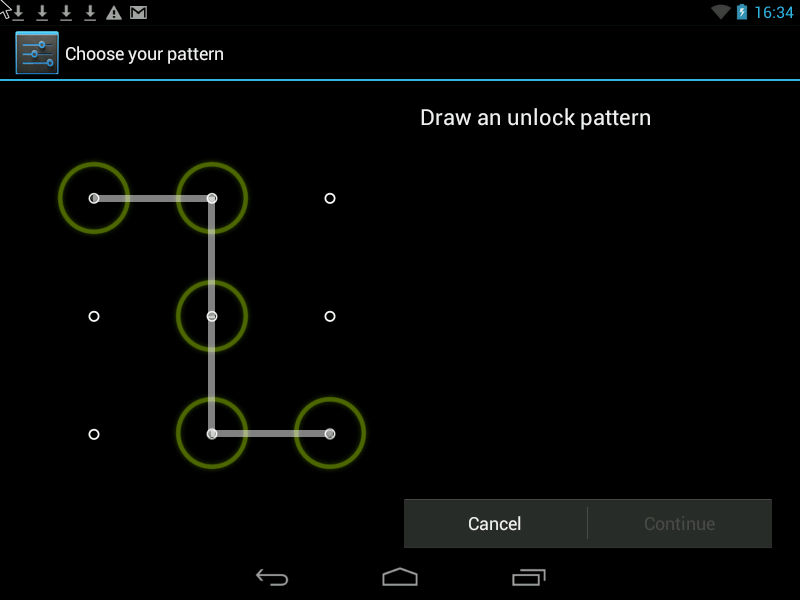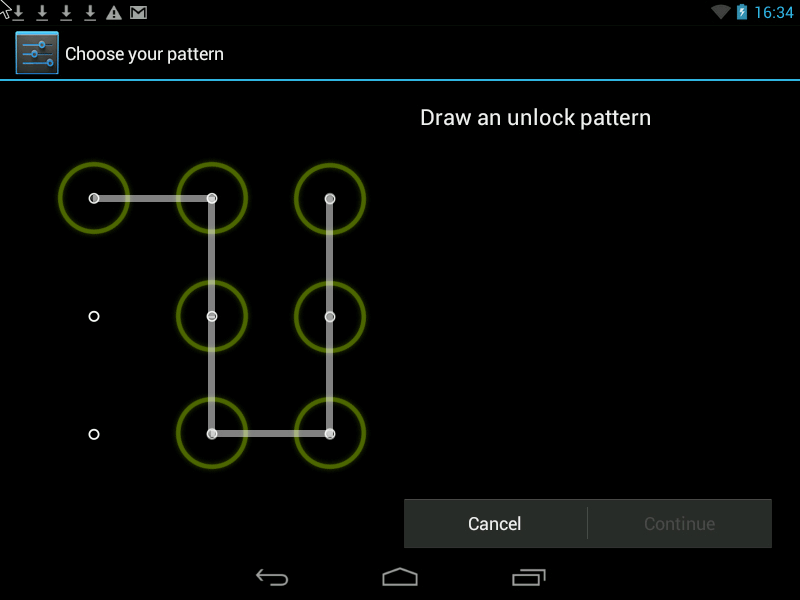
Graphic key
The essence of the presented method is that you need to connect a grid of points in any order. The minimum length of the curve should cover four points, the maximum consists of nine. The pattern path can be made either visible or invisible for even greater security.

What to do if you forgot your password or your phone is locked as a result of repeatedly entering the wrong pattern?
For any type of password, if you enter it incorrectly several times, the system will prompt you alternative way unlocking the phone. It will be enough to simply enter your username and password Google account, used in the device, after which you can change or reset the password. To do this, you can click on the “Forgot your pattern key?” button. below the unlock screen.
If you don’t remember your Google account password and login, you can go to https://accounts.google.com and click on the “Need help?” , and follow the suggestions to restore it. Next, provided that your device connects to the Internet after turning it on, you can enter a new password account and unlock the device.
There is a second way to reset the password, which will delete all data from the device and return it to its original state. In order to use it, you need to turn off the device by holding the power button, then while holding two volume buttons, briefly press the power button.
In the menu that appears on a black background, use the volume buttons to select the wipe data/factory reset option and confirm your choice by briefly pressing the power button. In the menu that opens, select yes and confirm the selection again by briefly pressing the power button. After this, the device will reboot, delete data and turn on in normal mode.
Some users are faced with the problem of Android devices being blocked by Privacy Protection mode. We will tell you what it is and describe the main methods for removing it from your phone.
The protection of personal data and confidentiality has recently become extremely important. Many manufacturers are trying to protect their devices from theft using various technologies. One of these technologies is the mode "Privacy Protection".
What kind of mode is this?
Please enter the Privacy Protection password to unlock- a special smartphone function that warns you about the need to enter a password to unlock the security mode. Mostly, this function Appears on phones after replacing SIM cards or running the screen for many hours with automatic dimming disabled.
Enter standard passwords will not help, here you need to specify the key set as the main one when connecting the phone anti-theft function. On many Chinese smartphones(Micromax, Alcatel, Doogee, etc.) the option is enabled by default, hence the problem.

Removing Privacy Protection
We dug around on the RuNet forums and identified several ways to unblock this mode. Some manage to do everything simply, while others had to re-flash the device via PC and install drivers.
- First try entering standard"factory" pin codes, which manufacturers most often set to this mode: 000000, 1234, 0000, 123456. If these pin codes do not work, move on to the next point.
- We request a password for your SIM card. The fact is that the phone can be linked to the user’s number (anti-theft option). The process is simple:
- remove the SIM card from the blocked device and insert another one, but with the balance in the account;
- install your card on another phone;
- reboot a phone blocked by Privacy Protection;
- messages will be sent to your card in Chinese, write the following characters in the response SMS - #mima#
- In response, you should receive a message with an 8-digit PIN code - enter them.
- If all the above methods turned out to be useless, you need to flash the firmware and reset the settings. You can find a lot of information about this on the Internet. I found a pretty good video tutorial on how to remove Privacy Protection from your phone.
As for the latter method, users have had a lot of controversy over the justification of this method. Some claim that they even erased their file using such a reset. phone imei. Everything is complicated in short.
If any of the methods helped you and you were able to remove Privacy Protection from your phone, please write in the comments. Please also tell me about other ways to remove the problem, if you have found them. Thank you.
Briefly: If you use a graphic key to access your phone, then 99% of the time this is enough to ensure that no one can access the information on your phone without your knowledge. If the data on your phone is very sensitive, then you should use the phone's built-in full encryption feature.
Today, almost all smartphones have become carriers of important personal or corporate data. Also, through the owner's phone, you can easily access his accounts, such as Gmail, DropBox, FaceBook and even corporate services. Therefore, to one degree or another, it is worth worrying about the confidentiality of this data and using special means to protect the phone from unauthorized access in the event of its theft or loss.
- From whom should you protect your phone data?
- Built-in data protection in Android.
- Full phone memory encryption
- Results
What information is stored on the phone and why protect it?
A smartphone or tablet often serves as a mobile secretary, freeing the owner’s head from storage large quantity important information. The phone book contains numbers of friends, co-workers, and family members. IN notebook they often write credit card numbers, access codes, passwords to social networks, e-mail and payment systems.
The list of recent calls is also very important.
Losing your phone can be a real disaster. Sometimes they are stolen specifically to penetrate personal life or to share profits with the owner.
Sometimes they are not stolen at all, but are used for a short time, unnoticed, but a few minutes is quite enough for an experienced malicious user to find out all the details.
The loss of confidential information can result in financial ruin, the collapse of your personal life, and the breakup of your family.
I wish I didn't have it! - the former owner will say. - It’s so good that you had him! - the attacker will say.
And so what needs to be protected on the phone:
- Accounts. This includes, for example, access to your mailbox gmail. If you have set up synchronization with facebook, dropbox, twitter. Logins and passwords for these systems are stored in open form in the phone profile folder /data/system/accounts.db.
- History of SMS correspondence and phone book also contain confidential information.
- Web browser program. The entire browser profile must be protected. It is known that Web Browser(built-in or third-party) remembers all passwords and logins for you. This is all stored in open form in the program profile folder in the phone’s memory. Moreover, usually the sites themselves (using cookies) remember you and leave access to your account open, even if you did not specify to remember the password.
If you are using sync mobile browser(Chrome, FireFox, Maxthon, etc.) with a desktop version of the browser to transfer bookmarks and passwords between devices, then you can assume that you can access all passwords from other sites from your phone. - Memory card. If you store confidential files on your memory card or download documents from the Internet. Typically, photos and videos taken are stored on a memory card.
- Photo album.
Who should you protect your phone data from:
- From a random person who finds your lost phonel because from “accidental” theft of the phone.
It is unlikely that the data on the phone will be of value to the new owner in this case. Therefore, even simple graphic key protection will ensure data safety. Most likely, the phone will simply be reformatted for reuse. - From prying eyes(co-workers/children/wives), who can gain access to your phone without your knowledge, taking advantage of your absence. Simple protection will ensure the safety of your data.
- Providing forced access
It happens that you are voluntarily forced to provide a phone number and open access to the system (information). For example, when your wife, government official or employee asks you to look at your phone service center Where did you take your phone for repair? In this case, any defense is useless. Although it is possible using additional programs, hide the fact of the presence of some information: hide part of the SMS correspondence, part of the contacts, some files. - From targeted theft of your phone.
For example, someone really wanted to know what was on your phone and made an effort to get it.
In this case, only full encryption of the phone and SD card helps.
Built-in data protection on Android devices .
1. Lock screen with Pattern Key.
This method is very effective in the first and second cases (protection against accidental loss of the phone and protection from prying eyes). If you accidentally lose your phone or forget it at work, no one will be able to use it. But if your phone purposefully fell into the wrong hands, then this is unlikely to save you. Hacking can even occur at the hardware level.
The screen can be locked with a password, PIN code and Pattern Key. You can select the locking method by launching the settings and selecting the Security -> Screen lock section.
Graphic Key (Pattern) - c the most convenient and at the same time reliable way phone protection.

None- lack of protection,
Slide— to unlock, you need to swipe your finger across the screen in a certain direction.
Pattern- this is a Graphic Key, it looks something like this:
You can improve security in two ways.
1. Enlarge the Graphic key input field. It can vary from 3x3 dots on the screen to 6x6 (Android 4.2 is found in some models, depending on the Android version and phone model).
2. Hide the display of the points and “path” of the graphic key on the smartphone screen so that it is impossible to peek at the key.
3. Set the screen to automatically lock after 1 minute of inactivity on the phone.
Attention!!! What happens if you forgot your pattern key:
- The number of incorrect attempts to draw a Graphic Key is limited to 5 times (in different phone models the number of attempts can be up to 10 times).
- After you have tried all your attempts but have not drawn the Pattern correctly, the phone is locked for 30 seconds. After this, you will most likely have a couple of attempts again, depending on your phone model and Android version.
- Next, the phone requests the login and password of your Gmail account, which is registered in the phone Accounts settings.
This method will only work if your phone or tablet is connected to the Internet. Otherwise deadlock or reboot to manufacturer settings.
It happens that the phone falls into the hands of a child - he starts playing, draws the key many times and this leads to the key being blocked.
PIN is a password consisting of several numbers.
And finally, Password— the most reliable protection, with the ability to use letters and numbers. If you decide to use a password, then you can enable the Phone encryption option.
Encryption of phone memory.
Feature included in the package Android versions 4.0* and higher. for tablets. But this feature may be missing in many budget phones.
Allows you to encrypt your phone's internal memory so that it can only be accessed with a password or PIN code. Encryption helps protect the information on your phone in the event ts
targeted theft. There is no way that attackers will be able to access your data from your phone.
A prerequisite for using encryption is to set a screen lock using a password.
This method achieves the preservation of user data located in the phone's memory, such as the phone book, browser settings, passwords used on the Internet, photos and videos that the user received using the camera and did not copy to the SD card.



— SD card encryption is enabled as a separate option.
— Memory encryption may take up to an hour depending on the amount of memory on the device. The phone cannot be used during encryption.
What if you forgot your password?
Password recovery is not provided in this case. You can do a full RESET on your phone or tablet, i.e. reinstall Android, but user data from the phone or tablet will be erased. Thus, if an attacker does not know the password to unlock the phone, he will not be able to use it. It will also be impossible to see data from the phone’s memory using other programs by connecting the phone to a computer, because all internal memory is encrypted. The only way to get your phone working again is to reformat it.
Attention, the full encryption function is present only starting from Android OS 4.0 - 4.1 and may simply not be available on some phone models. Most often found in phones from Samsung, HTC, LG, Sony. Some Chinese models also have an encryption function. On some phones this function is located in the “Memory” section.
Flaws:
- You will need to constantly enter a fairly complex password (6-10 characters) even if you just want to make a call. Although it is possible to set a long time interval (30 minutes) during which the password will not be requested when you turn on the phone screen. On some phone models, the minimum password length can be from 3 characters.
- On some phone models, it is not possible to disable encryption if you want to avoid having to constantly enter a password. Encryption can only be disabled by returning the phone to factory settings and erasing all data.
Encrypting an external SD memory card
The function is included in the standard Android 4.1.1 package for tablets. Missing from many budget builds.
The function provides reliable data protection on external SD card. Personal photos can be stored here, text files with commercial and personal information.
Allows you to encrypt files on an SD card without changing their names or file structure, while preserving preview graphic files (icons). The function requires setting a display lock password of at least 6 characters.




It is possible to cancel encryption. When changing the password, automatic re-encryption occurs.
If the user has lost the memory card, the encrypted files cannot be read through the card-reader. If you put it on another tablet with a different password, then the encrypted data also cannot be read.
Other Encryption Properties:
- Transparent encryption. If the card is inserted into the tablet and the user has unlocked the screen with a password, any application sees the files in decrypted form.
- If you connect the tablet via a USB cable to a computer, encrypted files can also be read on the computer by first unlocking the card from the screen of the mobile device.
- If you write some other unencrypted files onto the card via the card-reader, they will also be encrypted after inserting the card into the tablet.
- If you have an encrypted card, you cannot cancel the lock password.
- Data is encrypted at the file level (the file names are visible, but the contents of the file are encrypted).
Disadvantage of the program:O missing from most Android builds.
It should be emphasized that the best safety of data is a complete copy of it on your Computer in The smartphone is quite a fragile device small sizes, which means there is always a possibility of its breakdown or loss.
Improving the usability of a secure smartphone
Full phone encryption provides the strongest level of protection, but constantly entering a 6-digit password makes it difficult to use. But there is a solution.
IN Android system from version 4.2* it is possible to move some applications\widgets to the lock screen, and thus you can perform simple steps without constantly unlocking the phone (without entering a 6-digit password).
Results:
- The built-in and free features to protect your phone are very reliable. They are able to protect against prying eyes the user’s contacts, his correspondence and calls, accounts in various programs and networks, as well as files and folders located both in the phone’s memory and on a removable SD card.
- Before buying a phone, you should make sure how the required protection works in this particular phone model: the requirement to use an overly complex PIN code or password on the lock screen (Pattern Key is not suitable), irreversible encryption internal memory phone, i.e. the only way giving up encryption is full reset phone settings.
- Important! Make sure that if you forget your password or pattern key, you can restore access to your phone or you can easily restore your phone settings and information if you have to hard reset(resetting the phone to factory settings with loss of all data).
- Keep backup copy confidential data is required only on your Computer, on DVD disc or in the cloud.
