Control of remote user actions. Tracking on a computer using the Jetlogger keylogger program
Rating: 3.9 out of 5
Votes: 15 NeoSpy - simple and convenient program to covertly monitor the actions of a computer user.
Main features of the program:
- Keeps records of programs launched on your computer.
- Takes and saves screenshots (screenshots)
- Saves everything that was typed on the keyboard into a report ( keylogger)
- Keeps a log of connecting / disconnecting to the Internet
- Monitors any changes in file system(creating, deleting, changing files)
- Monitoring of incoming and outgoing Internet traffic
- Tracks website visits (date, time, Web pages viewed)
- Controls the contents of the clipboard
- Saves the history of incoming/outgoing messages and passwords of any icq clients (icq, icqlite, qip, miranda, &RQ and others)
- Saves a list of folders in the user profile (for example, you can find out where “My Documents” are located for a specific user)
- Saves a list of programs installed by the user
- Intercepts passwords to accounts Windows
- Monitors Mail-agent (mail.ru) messages and passwords
- Monitors USB drives (saves files copied to a flash drive)
- Controls the output of documents for printing, monitors the operation of printers, and saves printed documents.
It is possible to view the work of other network users in real time (user actions and viewing desktop status). To configure the user monitoring mode over the network, you must install the NeoSpy program on the monitored computers.
With the help of this program, you can always control how your employees spend their working time.
NeoSpy stores all collected data (reports) on your computer, and it is also possible to send all program reports to your e-mail.
NeoSpy can be launched in both normal (visible) and hidden mode (the program is not visible in the tray or in the task manager process list).
It is possible to set a password for access to the program settings and reports, as well as enable the autorun option (start the program together with starting Windows).
NeoSpy is great for monitoring office computers, and PC homework in your absence. The product will be useful to company managers system administrators And active users PC.
The product is fully compatible with the entire Windows line (98, ME, NT, XP, 2003, Vista, Seven)
Tracking a user by secretly installing a keylogger program on his computer is not only a low moral act, but also a criminal offense. However, the situation changes radically when it comes to parents monitoring their children and monitoring by the management of organizations the activities of their employees. In both cases, the object of tracking will not be the full owners of the computers, but the persons to whom the equipment has been entrusted with certain restrictions. Children can use the computer within age restrictions. And company employees are required to use the devices entrusted to them for the duration of their work only to perform official tasks. The employer has the right to periodically check the performance of his employees. But parents not only have the right, they are obliged to monitor the fragile psyche of their children, which can be disturbed by both banal rudeness on Internet forums and blogs, and serious things like porn, games promoting violence, teenage trolling on social networks, etc. For parents and employers supervising their children and employees, respectively, the developers Jetlogger programs and created their own product - a keylogger that operates invisibly in Windows environment. The Jetlogger program will be discussed further.
Important: The use of spyware as a tool to steal confidential information and for other illegal purposes entails criminal liability.
1. About the program
Jetlogger is more complex than programs like parental controls because it works unnoticed by the user and allows you to track his actions in the finest detail. Jetlogger can do a lot, the program:
- collects information about all programs, games, and open sites running on the computer;
- monitors queries entered into search engines;
- keeps track of time spent on specific programs, games and sites;
- records the total time of activity at the computer;
- remembers the text typed on the keyboard;
- monitors the clipboard, created and edited files;
- after a certain period of time takes screenshots of the entire screen and photos from the webcam;
- provides 4 mechanisms for delivering work reports, as well as a mode remote access with real-time tracking of user actions.
All these functions can be tested for free in the trial version of Jetlogger for a month. The only limitation of the trial version is the inability to actually use the program due to a demonstrative notification that the computer is in tracking mode in the upper right corner of the screen.
The notification will disappear after activating the program. Jetlogger is distributed across paid subscription, the cost of which is 680 rubles. per month. An annual subscription is several times cheaper - 240 rubles. per month, but keep in mind that this option may be a waste of money if the keylogger is detected and removed from the system.
2. Install Jetlogger
At the first stage of installing the program, click the “Settings” option.
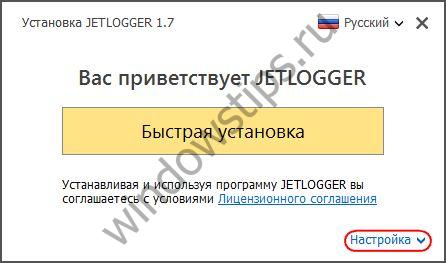
Jetlogger doesn't install like regular program: its files will be placed in hidden folder on drive C “ProgramData”, it will not appear in the list of uninstaller programs and in startup. Autostart of Jetlogger is not initially provided, but is configured inside the program and right at the stage of its installation.

To launch the program at first, it is intended regular shortcut on the desktop. After studying the specifics of Jetlogger and the hot keys for opening it, the shortcut on the desktop is correspondingly destroyed. But before you start studying the program, you need to do some work in the system.
3. Adding Jetlogger to antivirus exceptions
The creators of Jetlogger claim that their brainchild, despite the fact that it is spyware, is not recognized as malware by antivirus software installed on computers in 95% of cases. The creators do not say what specific anti-virus products they are talking about, but it has been experimentally verified that these 95% definitely do not include the standard Windows Defender 10. It blocks Jetlogger literally a couple of minutes after installing it. So in any case, at the next stage after installing the program, you need to add the folder along the path to the exclusion list (aka white sheet) of the antivirus:
C:\ProgramData\JetProject
4. Settings
Having launched Jetlogger, first turn to the “Settings” section. In the first tab “Basic” we can assign autorun if this function was not enabled during installation, and change the preset hotkeys for opening the program. Any changes to the settings must be additionally confirmed with the save option at the bottom of the window.
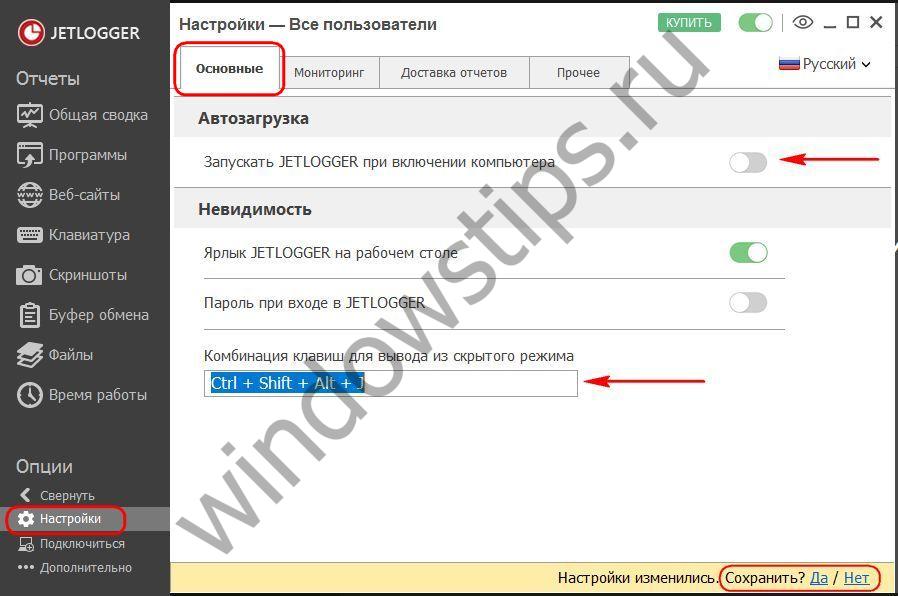 4
4 The second tab “Monitoring” is intended for setting up individual types of monitored data - screenshots and webcams, programs used, sites visited, files operated on, etc. Any type of monitored data can be disabled if it is not of interest or consumes too much system data. resources. Some types of tracked data are additionally configurable. Thus, for webcam images and screenshots, you can change the conditions for their creation. The latter, depending on the capabilities of the computer, can be created in worse or better quality. Snapshot storage can be limited to a certain amount of disk space.
 5
5 Tracking operations with files provides the ability to refuse tracking of individual actions such as creation, deletion, modification, renaming. To capture data entered from the keyboard, you can configure the storage of hot key combinations.
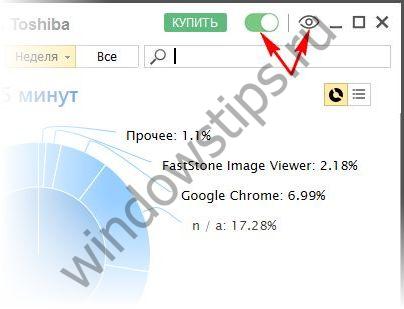
5. Enable tracking
The tracking process is turned on and off using the green toggle button at the top of the window. Nearby there is a button in the shape of an eye; it is responsible for transitioning Jetlogger to hidden mode, the exit from which after deleting the program shortcut, we recall, is carried out using hot keys.
6. Report display
The data tracked by the keylogger will be displayed in the corresponding sections of the report.
 7
7  8
8 7. Delivery of tracking reports
Let's go back to the program settings. In the “Report Delivery” tab, Jetlogger can be configured to automatically send reports after a certain period of time, at specified time, when the computer is idle or turned off. Reports can be sent to email, FTP server, to cloud storage. Reports can also be saved in a specific folder on your computer that can be hidden.
 9
9 Sent by email or FTP, to the cloud or a folder on your computer, the report will contain captured images, as well as an HTML file with an activity graph and a detailed list of tracked actions.
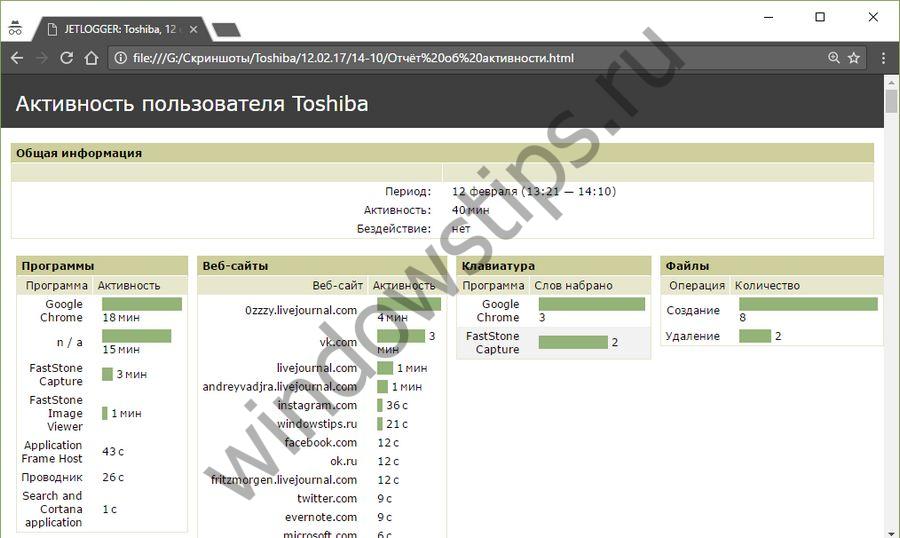 10
10 Jetlogger tracking reports can be viewed remotely - in the program interface installed on another computer. The remote connection is made using cloud storage. In this case, reports will be updated in real time. But to do this, you initially need to make some settings in Jetlogger on the computer of the tracking object. Click “Connect” at the bottom, then “Start”.
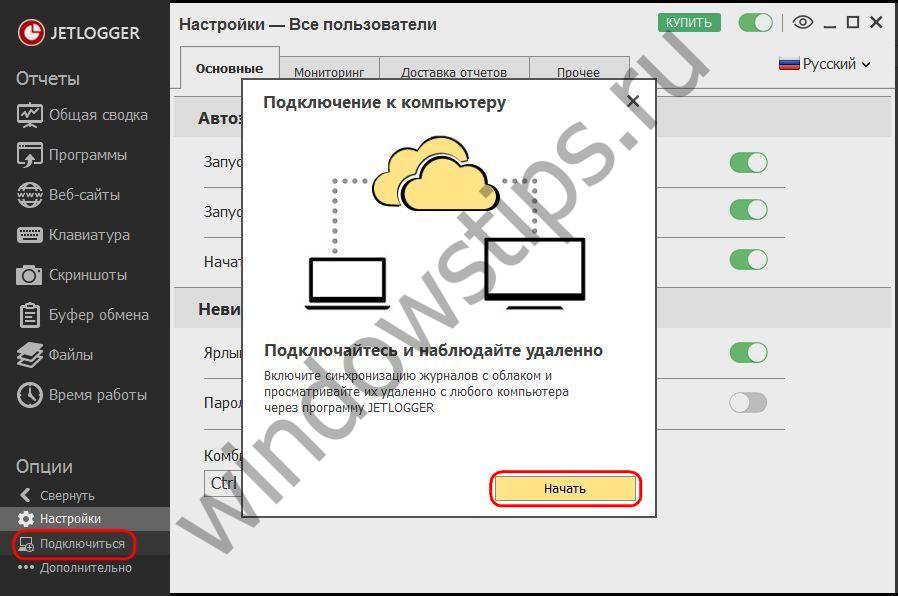 11
11 Of the two possible actions, select “Allow connections to this computer.” In the drop-down list, select any of the cloud storages supported by the program and enter authorization data.
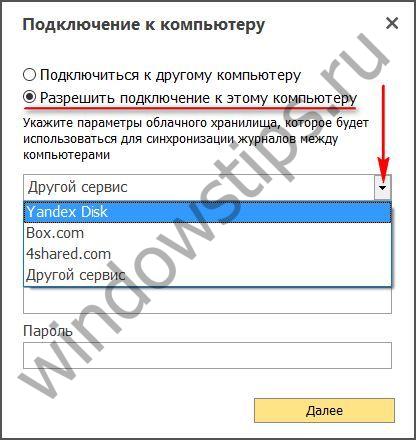

These IDs and passwords must then be entered into Jetlogger at remote computer to access program data on the computer of the target being tracked. On the remote computer, also click “Connect”, only select the “Connect to another computer” option. Enter your ID and password and click the “Connect” button.
 14
14 After which the tracked data will be displayed in the program interface current computer, and the computer of the tracking object.
8. Computer performance
Spies usually slow down Windows operation, and Jetlogger is no exception in this regard. The program was tested on a computer with average hardware characteristics, and the decrease in system performance when the tracking function was enabled immediately became noticeable. Before deciding to purchase a program license, it is advisable to thoroughly test its operation. specific device. If there is a noticeable deterioration in performance, it may make sense to stop Jetlogger from capturing certain types of data. So, in the event of a sharp decrease in computer performance, the tracking object may suspect the presence of malware and scan the computer with anti-virus utilities or LiveDisk, which will block Jetlogger.
9. Uninstall Jetlogger
As mentioned, Jetlogger does not appear in the list of uninstallers. Uninstallation of a program is provided within the program itself – in the “Advanced” section.
 15
15 Have a great day!
